Newsletter 28th March 2020 – Cyber Security 2
Hello ?
Viruses come in many forms these days
Once again, we return to Cyber Security as many of us are at home and using the internet under different relaxed conditions, we have time to open the emails we would not normally open.
I would like to draw your attention to Elite’s previous newsletter on Cyber Security on 28th December 2018 which can be found on our blog website www.elite-security-systems.info
Suspicious emails should be moved to the JUNK/SPAM box and then opened as all links will be made inoperable and safer than opening in your INBOX to evaluate and identify whether it is phishing or not.
Links could have an identifying code, that you can identify the URL of the website they are sending you to, if in doubt open a web browser and type in the web address (not the full link) of the website concerned. Once on the website you can ascertain that it is the correct website, probably because you have typed in the URL you know for that website. Then search for the offer or page that the email you received was pointing you to. In the case of Elite’s websites we have our main www.elite-security-systems.co.uk and the Blog is www.elite-security-systems.info both have links to lead from one to the other.
You will notice near the end of this document there are three different ways of subscribing to get these monthly newsletter in your inbox, the link does not necessarily show the website address but you know the name of the company ie Elite Security Systems that this document refers to.
Two Factor Authentication
A second form of authentication for logging into a website, email account or devices is always better than just a single login.
Multi or Two-factor authentication (also known as 2FA) is a type, or subset, of multi-factor authentication. It is a method of confirming the users’ stated identities by using a combination of two different factors: 1) a bit of something they know, 2) a bit of something they have, or 3) a bit of something they are.
Smart phones for example can require biometric fingerprint to open the phone to APPs, but then you can also add the extra layer, to open an APP, again requires your fingerprint.
Authentication APP, these are used to formulate a random six-digit code that is changed every thirty seconds. Companies that use these for transfer of money are offering this as well as many other websites just to ensure secure login. Paypal, Facebook, Microsoft are just some of the users.
Cyber Attack
Earlier this year in February it was revealed that there was a huge cyber-attack of the MGM Resorts.

10.6 million guest’s personal information had been hacked in 2019. Names, addresses birth dates, phone numbers and passport numbers had been stolen. Some quite prominent people’s information was involved.
As reported by tech site ZDNet before MGM confirmed the attack to the BBC, the data was posted to a hacking forum in February 2020.
MGM Resorts spokesperson said: “Last summer, we discovered unauthorised access to a cloud server that contained a limited amount of information for certain previous guests of MGM Resorts. We are confident that no financial, payment card or password data was involved in this matter.”
Ed Macnair, CEO of Censornet commented his concern that the stolen information would now be used in a fresh wave of attacks.
Cloud servers have been a regular feature in many of the larger data breach stories we have seen recently. In this case, it appears that criminals gained unauthorised access, (Access was gained through maybe a leaked password or phishing) which allowed them to extract data such as names, addresses and passport details etc. It’s a blunt reminder of the risk that comes with cloud transformation, in the past this data would have been held on the hotel’s own servers. In many ways, moving to the cloud has corroded the conventional perimeters that protected data, so companies need to make sure they have new security practices for the cloud. A lapse in security can lead to so much misery and confusion.
Companies can have comprehensive penetrations testing to evaluate the security of there networks and systems, also staff’s perception of incoming communications or usage and their resulting actions that may contribute to a risk to the cyber security of the company.
ZDNet also reported this week that Hackers breach FSB contractor and leak details about IoT hacking project
Russian hacker group Digital Revolution alleges they have breached a contractor for the FSB, Russia’s national intelligence service, the contractor was building an IoT botnet and Digital Revolution uncovered details about a project aimed for hacking Internet of Things (IoT) devices.
The group published this week 12 technical documents, diagrams, and code fragments for a project called “Fronton.”
ZDNet has also viewed the documents personally, along with BBC Russia, who first broke the news earlier this week.
So, ladies and gentlemen this happens to the large and small, we need to be aware of what can happen if you’re not careful on the internet.
Today’s security risks have increased in scale and importance. There can now be billions of pounds/dollars at risk when information security isn’t controlled properly.
Stay safe from Viruses of all kinds.
SPECIAL OFFER
Mini Biometric Fingerprint Padlock
Suitable for locking a host of things including that laptop case or luggage not that anyone is going anywhere in this current climate of things.
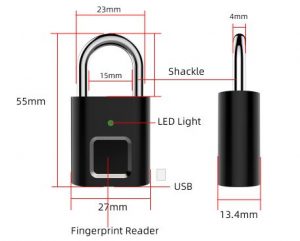
Cost £22.49 including P & P in the UK
Email your order to: info@elite-security-systems.co.uk
Subscribe to our newsletter for this direct to your inbox at
Subscribe
http://eepurl.com/dxBpJr
www.elite-security-systems.info and look for the signup page to subscribe at the bottom of the home page.
Thank you for reading
Kind regards
Marketing Department